Laying the Groundwork For Trusted Cyber Secure Ecosystems
CIP Security is evolving into a more robust security framework and adding solutions for device authentication and hardening.
June 7, 2016
Industrial control systems have traditionally set its overall priorities as safety first and production availability next. But what is interesting now is that security, driven by the threat of cyberattacks, has moved forward and needs to be balanced with these first two priorities.
For industry, where in the past cyberattacks have been hard and focus on Stuxnet as the first high-profile example, there are now more damaging attacks coming to light. A cyberattack reported by the German government in December 2014 reported that a mill actually suffered damage because the control systems were compromised such that a blast furnace could not be shutdown, causing physical damage to the site.
“There has been not only an awareness that threats not only can occur but an admission that it’s not a matter of if but when,” Nancy Cam-Winget, distinguished engineer at Cisco Systems, told Design News. “The need for education is more at the forefront and more accepted, where in the past there was more of a tendency to wait.
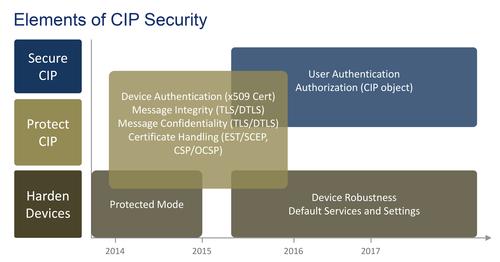
The timeline for CIP security developments has a focus on software technologies for user authentication and authorization, along with hardening of devices.
(Source: ODVA)
“As an industry, we’re trying to take more responsibility and be more proactive,” Cam-Winget said. “ODVA recently published a new set of specifications, and there is a new focus on CIP security. When you look at the critical infrastructure functions that NIST published, and when you look at the nuts and bolts of the lifecycle of any security framework, they all distill to the same sets of functions.”
The NIST set of security functions outlines a series of steps: identification, protection, detection, response, and then mitigation or recovery. Cisco has simplified its model into three parts: before, during, and after. First, there is a defense able to identify threats and provide protection mechanisms. But with detection, in part because systems have become so porous with respect to connectivity and communications, there is a need for continuous monitoring. That’s where detection comes in and, as part of the “during” phase, continues even while the systems are up and running. But after that, as part of the continuous monitoring, there also needs to be a focus on continuous process improvement.
 Stay Secure. Learn more about managing cyber security and hacking in the world of smart plants, sensor-rich IoT, and more at Industry 4.0: Smart Manufacturing, part of Atlantic Design & Manufacturing Expo, June 16 in New York. Register here for the event, hosted by Design News’ parent company UBM. Enter promo NY16DN for a FREE Expo pass & 20% off Industry 4.0 Conference.
Stay Secure. Learn more about managing cyber security and hacking in the world of smart plants, sensor-rich IoT, and more at Industry 4.0: Smart Manufacturing, part of Atlantic Design & Manufacturing Expo, June 16 in New York. Register here for the event, hosted by Design News’ parent company UBM. Enter promo NY16DN for a FREE Expo pass & 20% off Industry 4.0 Conference.
OT Lagging Behind
“For industry, if you compare information technology security versus operations technology security, OT security is lagging by a couple of generations,” Cam-Winget said. “When you look at the lifecycle of how to secure and protect industrial control systems, the first step is visibility and the ability to identify threats so you can put the appropriate protection mechanisms in place. That is where CIP security is beginning to focus.”
Within the CIP security specification, there are already mechanisms for creating (security) profiles and levels of security, but it also points out the need to identify devices. From a greenfield standpoint, a utopian view would say that everything has an immutable identity, but legacy equipment poses a challenge. But with operations technology, even though companies often can’t afford to uproot everything, CIP security provides a way to move forward.
You May Also Like

.jpg?width=300&auto=webp&quality=80&disable=upscale)

