Does your IoT device pass the UL test?
UL now offers security certification to help IoT device makers satisfy customer concerns and meet forthcoming state regulations.
November 27, 2019

Consumers are quickly losing trust in the IoT due to numerous security breaches from relatively simple attacks. Examples abound, such as smart LED light bulbs that leaked Wi-Fi passwords, or an Internet-connected thermometer in a Casino lobby aquarium that enabled hackers to access its network and extract sensitive client information. The list of easily hackable IoT devices goes on to include everything from IoT sex toys and medical devices to smart phone enabled locks, rooftop weathervanes, and more.
All of these breaches were made possible by rather fundamental security mistakes.
“A lot of security issues are due to common problems – default passwords, poor communication security, poorly maintained software – and that’s what we’re trying to address with our IoT Rating program.” noted Andrew Jamieson, the Director of Technology and Security for UL’s security testing division. “UL’s mission is making the world a safer place, and these days that includes making sure IoT systems are secure.”
In addition to seriously affecting customer willingness to trust IoT technology, these hacks have tarnished company brand value, sales and revenues. With so many inconsistently secured devices, it is easy to see why the IoT is leading to a new category of cybercrime.
Manufactures have found little guidance from professional or national organizations for acceptable security practices for the sensors, devices, mobile phones, gateways and servers that make up the IoT. True, NIST recently issued a Core Cybersecurity Feature Baseline for Securable IoT Devices (Draft NISTIR 8259), which provides voluntary guidance intended to help promote the best available practices for mitigating risks to IoT security. It complements NIST’s Considerations for Managing Internet of Things Cybersecurity and Privacy Risks (NISTIR 8228), which primarily addresses large organizations that have more resources to dedicate to IoT cybersecurity.
|
Image Source: NIST - NISTIR 8228 IoT road map |
But the NIST guidelines are intended for corporate enterprises and government agencies, not IoT manufactures and vendors. Without consistent rules and ways to gauge compliance for cybersecurity protection, manufactures are left to their own approaches and consumers are left in confusion when comparing security features between competing vendors.
This is the problem that UL, a global safety testing lab, is trying to address with its recently released IoT Security Rating Solutions. This rating will help manufacturers demonstrate their proven adherence to cybersecurity best practices. For consumers, this will give an easy to understand rating level listed on product labels, similar to existing ones that certify safety compliance for household electrical cables.
Further, the IoT Security Rating will be essential for manufactures to comply with upcoming regulations. Legislation in California (Senate Bill 327) and Oregon (House Bill 2395) will hold U.S. manufacturers responsible for adding “reasonable security features” in devices or physical objects that are able to connect to the internet directly or indirectly. Both bills become effective Jan. 1, 2020.
5 Priorities
A UL “IOT Security – Top 20 Design Principles” whitepaper describes critical principals that can be taken to increase the security of connected systems. The first five of these principals – or steps – are perhaps the most important:
Provide a manual override for any safety-critical operations.
Ensure parameters which could compromise the system (secret or private cryptographic keys, passwords, etc.) are unique per device.
Test the system to be sure it is free of known, exploitable vulnerabilities prior to release.
Allow for software updates and ensure they are cryptographically authenticated prior to installation and execution. Implement anti-rollback features to prevent the installation of previous vulnerable versions of firmware.
Use industry standard security protocols with best practice defaults for any remote or wireless connections and authentication of connections to management services.
Applying these steps, as well as the other 15 listed in the UL whitepaper, will improve a company’s security rating. The requirements of this whitepaper were used as input to the creation of the UL IoT Security Rating solution, further developed through mapping against other industry baselines and best practices (details of which can be found here). As freely available documents, anyone can review and test against these – although if you want a rating and UL Verified Mark based on compliance to the program requirements you will need the testing to be performed by UL.
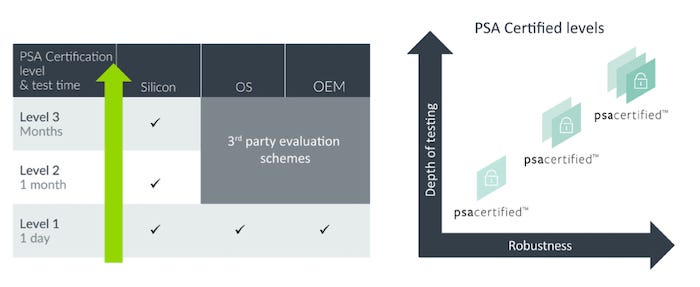
Other programs for IoT security include the Platform Security Architecture (PSA) framework established by hardware processor giant Arm and test labs such as UL, Riscure, and Brightsight. The PSA framework is comprised of two elements: a multi-level security robustness scheme and a developer focused API test suite. The security testing is based on third-party lab-based evaluation that is intended to build trust through independent checking of the generic parts of an IoT platform including: PSA Root of Trust (the Root of Trust is the source of integrity and confidentiality), the real-time operating system (RTOS) and the device itself, according to ARM. There are three progressive levels of security certification.
|
Image Source: ARM |
IEEE (Non-manufacturing) IoT Standards
Both of these programs are intended to help manufacturers and vendors of IoT devices design and build secure products, but address this problem in different ways. The UL IoT Security Rating solution aims to provide information to customers at the point of purchase about how secure the product is, so that they can build that into their purchase decision – addressing the commercial aspect of the security problem. The ARM PSA program aims to help vendors build security into their systems from the ground up, ensuring that everything from the silicon upwards is built on a secure base. If you are an Electronic Engineers actually designing IoT systems, then you’ll want to check out the latest IEEE standards that address the technical “vibrancy” of IoT systems:
Architectural framework: The focus of IEEE P2413 is to develop a standard for the architectural framework for the Internet of Things, which includes descriptions of various IoT domains, definitions of IoT domain abstractions, and identification of commonalities between different IoT domains. The architectural framework defined in this standard will promote cross-domain interaction, aid system interoperability and functional compatibility.
Harmonization and security of IoT: The IEEE 1451-99 is focused on developing a standard for harmonization of Internet of Things (IoT) devices and systems. This standard defines a method for data sharing, interoperability, and security of messages over a network, where sensors, actuators and other devices can interoperate, regardless of underlying communication technology.
Sensor Performance and Quality: Sensors are fundamental to IoT ecosystem with large volume of different sensors integrated into a complex framework. IEEE 2700 proposes a common framework for sensor performance specification terminology, units, conditions and limits is provided. IEEE P2510 defines quality measures, controls, parameters and definitions for sensor data related to Internet of Things (IoT) implementations.
The new UL offered IoT Security Rating will provide evidence that manufacturers meets standard best practices for IoT security, an important measure that supports upcoming security legislation. Further, this UL rating system should help consumers re-establish trust that their IoT devices meet a minimum of security robustness.
John Blyler is a Design News senior editor, covering the electronics and advanced manufacturing spaces. With a BS in Engineering Physics and an MS in Electrical Engineering, he has years of hardware-software-network systems experience as an editor and engineer within the advanced manufacturing, IoT and semiconductor industries. John has co-authored books related to system engineering and electronics for IEEE, Wiley, and Elsevier.
About the Author(s)
You May Also Like